Difference between revisions of "Auditing Windows Server 2008 File and Folder Access"
m (Text replacement - "<google>BUY_WINSERV_2008</google>" to "<htmlet>win2008</htmlet>") |
m (Text replacement - "<table border="0" cellspacing="0">" to "<table border="0" cellspacing="0" width="100%">") |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 51: | Line 51: | ||
| − | < | + | <htmlet>win2008</htmlet> |
Latest revision as of 19:59, 27 October 2016
| Previous | Table of Contents | Next |
| Understanding Windows Server 2008 File and Folder Ownership and Permissions | Configuring Volume Shadow Copy on Windows Server 2008 |
| Purchase and download the full PDF and ePub versions of this eBook only $9.99 |
In order to track file and folder access on Windows Server 2008 it is necessary to enable file and folder auditing and then identify the files and folders that are to be audited. Once correctly configured, the server security logs will then contain information about attempts to access or otherwise manipulate the designated files and folders. It is important to note that file and folder auditing is only available for NTFS volumes.
Enabling File and Folder Auditing
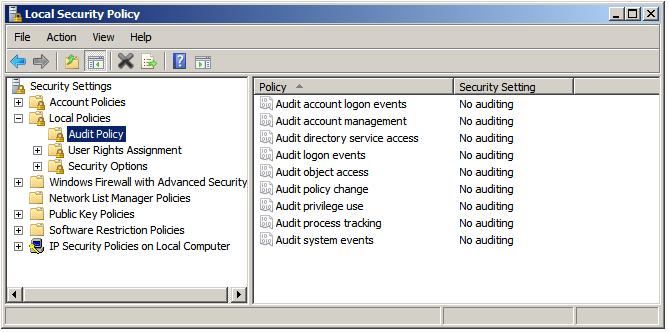
File and folder auditing is enabled and disabled using either Group Policy (for auditing domains, sites and organizational units) or local security policy (for single servers). To enable file and folder auditing for a single server, select Start -> All Programs -> Administrative Tools -> Local Security Policy. In the Local Security Policy tool, expand the Local Policies branch of the tree and select Audit Policy.
Double click on the Audit Object Access item in the list to display the corresponding properties page and choose whether successful, failed, or both types of access to files or folders may be audited:
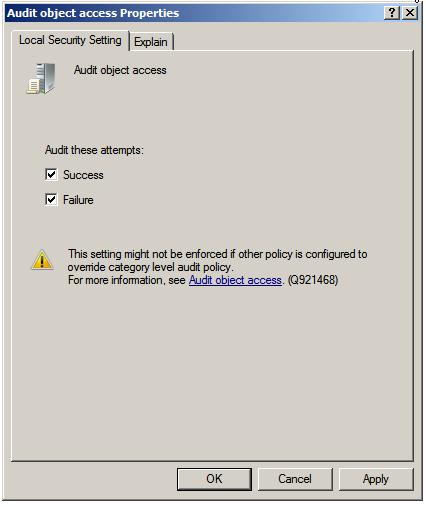
Once the settings are configured click on Apply to commit the changes and then OK to close the properties dialog. With file and folder auditing enabled the next task is to select which files and folders are to be audited.
Configuring which Files and Folders are to be Audited
<google>WIN28BOX</google> Once file and folder access auditing has been enabled the next step is to configure which files and folders are to be audited. As with permissions, auditing settings are inherited unless otherwise specified. By default, configuring auditing on a folder will result in access to all child subfolders and files also being audited. Just as with inherited permissions, the inheritance of auditing settings can be tuned off for either all, or individual files and folders.
To configure auditing for a specific file or folder begin by right clicking on it in Windows Explorer and selecting Properties. In the properties dialog, select the Security tab and click on Advanced. In the Advanced Security Settings dialog select the Auditing tab. Auditing requires elevated privileges. If not already logged in as an administrator click the Continue button to elevate privileges for the current task. At this point, the Auditing dialog will display the Auditing entries list containing any users and groups for which auditing has been enabled as shown below:
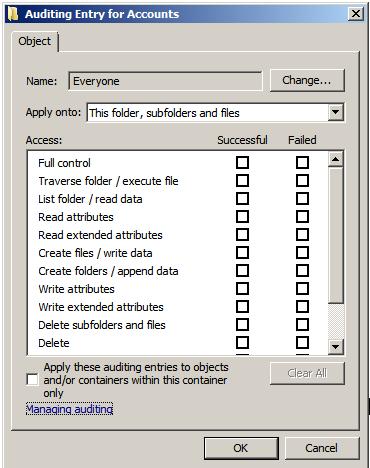
To add new users or groups whose access attempts to the select file or folder are to be audited click on the Add...' button to access the Select User or Group dialog. Enter the names of groups or users to audit, or Everyone to audit access attempts by all users. Click on OK to display the Auditing Entries for dialog as illustrated below:
Use the drop down list to control whether the auditing setting is to be applied to the current file or folder, or whether it should propagate down to all children files and/or sub-folders. Finally, select which types of access are to be audited and, for each type, whether successful, failed or both kinds of attempt are to be audited. Once configured, click on OK to dismiss current dialog and then Apply the new auditing settings in the Auditing Entries dialog.
From this point on, access attempts on the selected file or folder by the specified users and groups of the types specified will be recorded in the server's security logs which may be accessed using the Events Viewer, accessible from Computer Management.
| Purchase and download the full PDF and ePub versions of this eBook only $9.99 |