Difference between revisions of "Basic RHEL 5 Firewall Configuration"
(New page: A firewall is a vital component in protecting a computer system, or network of computers from external attack (typically from attack via an internet connection). Any computer connected dir...) |
(No difference)
|
Revision as of 17:14, 28 July 2010
A firewall is a vital component in protecting a computer system, or network of computers from external attack (typically from attack via an internet connection). Any computer connected directly to an internet connection must run a firewall to protect against malicious activity. Similarly, any internal network must have some form of firewall between it and an external internet connection.
In keeping with other Linux distributions, Red Hat Enterprise Linux 5 is supplied with powerful firewall technology known as iptables built-in. Entire books can, and indeed have, been written about configuring iptables. If you would like to learn about iptables we recommend Linux Firewall Configuration - Packet Filtering and iptables which can be found online at:
http://www.linuxtopia.org/Linux_Firewall_iptables/index.html
Fortunately RHEL 5 also provides some tools that make firewall configuration easy for the average user. This chapter will cover the steps necessary to configure an RHEL 5 firewall using those tools.
Configuring a Basic RHEL 5 Firewall
To launch the standard RHEL 5 firewall configuration tool, open the desktop System menu and click on Administration followed by Security Level and Firewall. Alternatively, the tool can be launched from the command-line as follows:
system-config-securitylevel
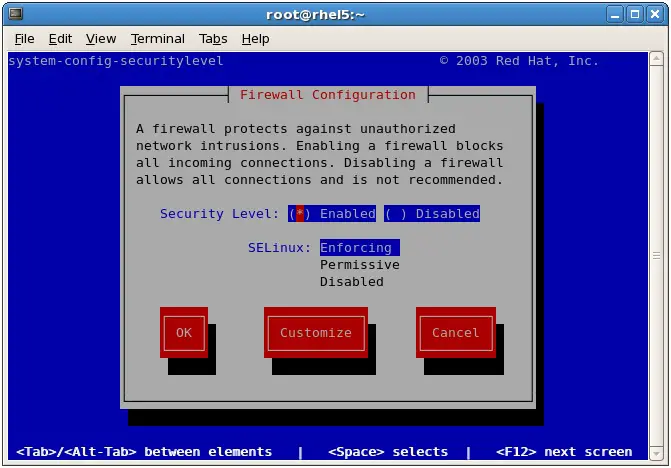
Enter the root password if prompted to do so. Once loaded, the security level tool should appear as follows:
Enabling and Disabling the Firewall
By default, the firewall will be active on a newly installed RHEL system. This is the preferred state for the firewall unless the system is running within a secure network environment or has no network connection. To enable or disable the firewall, select the corresponding option from the Firewall drop down menu. Clicking on the Apply button after making a change to this setting will commit the change.
Configuring Firewall Port Settings
The main area of the Security Level Configuration tool consists of a list of TCP/IP based services. Next to each entry is a check box that controls whether the service is trusted, and as such whether or not the corresponding TCP/IP port is open to traffic on the firewall or not (such as port 80 for a web server).
A summary of the primary services is as follows:
- SSH - The secure shell provides an encrypted mechanism for allowing password protected remote access to your system. With SSH you can remotely log into to your system, copy files between your system and other systems and perform remote execution of programs. If you need remote access to your system you will need to activate this. If you do not need remote access leave this disabled.
- Telnet - Telnet provides remote terminal access to your system. It does not use encryption and use is strongly discouraged. Leave this disabled and use SSH instead for remote access.
- WWW (HTTP) - If you are hosting a web server on your RHEL system you will need to enable HTTP traffic through the firewall to enable web page requests to reach the http server. If you do not plan to host a web server, leave this disabled.
- Mail (SMTP) - Specifies whether the firewall blocks Simple Mail Transfer Protocol traffic. This is only necessary if you are hosting a mail server on your RHEL system. If you only use a mail client to download email from a POP3 or IMAP server you can safely leave this disabled.
- FTP - Controls whether File Transfer Protocol traffic is permitted through the firewall. Unless you plan to set up an ftp server (unlikely for typical users) leave this option disabled.
- Samba - The Samba service allows files and printers to be shared between Linux and Windows systems. If this traffic is blocked in the firewall, it will not be possible to use Samba on this system.
A more extensive list of services and ports can be found on-line at:
http://www.techotopia.com/index.php/Primary_TCP/IP_Port_Assignments_and_Descriptions]
To activate or deactivate an option simply click on the check box next to the service. Once the required settings have been configured, click on the Apply button to commit the changes to the system.
Configuring Other Ports
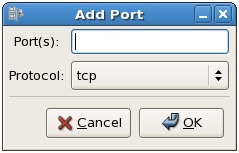
The list of well known ports are not, of course, the only ports available. In fact there are thousands of ports available for use by applications and services. To open a specific port, use the Other ports category of the Security Level Configuration tool. To open a port, click on the Add button to display the Port and Protocol dialog shown below:
To open a port to traffic through the firewall, simply enter the port number and select the corresponding protocol (TCP or UDP) from the menu and click on OK. On returning to the main configuration screen, select Apply to commit the change to the firewall.
Firewall Configuration from a Terminal using lokkit
In addition to the graphical Security Level Configuration tool, RHEL also includes the lokkit command-line firewall configuration tool that enables configuration changes to be made from a terminal window.
To launch lokkit, start a terminal session to access the command prompt (right click on the desktop background and select Terminal from the resulting menu) and type the following at the command-line prompt:
su – lokkit
Enter your password when prompted. Once loaded, lokkit should appear as follows:
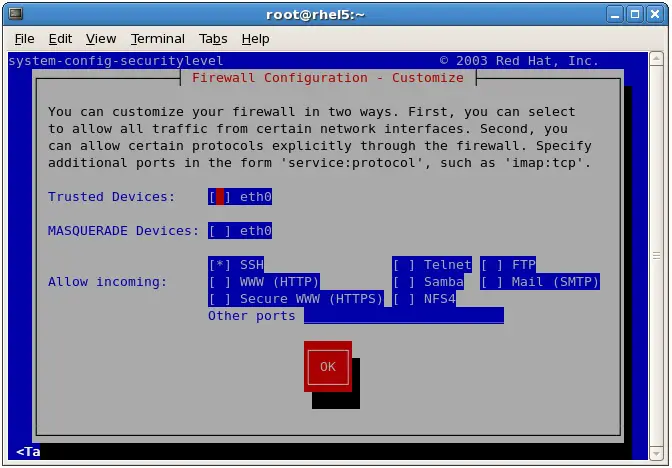
The most useful lokkit screen is the customization screen. To access this screen use the Tab key to navigate to the Customize button at the bottom of the screen. Once Customize is highlighted, press the Enter or Space key to select it. The Customization screen should appear as follows:
To activate or deactivate an option use the Tab key to navigate to the required option and press the space bar to toggle the selection. Activated options are marked with an asterisk (*).
To specify a specific port, enter the port number and protocol into the Other ports field in the form of port:protocol. When you have finished making selections tab to the OK button to return to the main screen and tab to OK again to exit lokkit.
The customization screen of the lokkit tool also allows trusted interfaces and masquerading to be configured.
Trusted Interfaces
A trusted interface is a network adapter (either physical or software based) on which traffic is known to be coming from a secure network environment. For example, an RHEL system acting as a firewall for an internal network might contain two network adapters, one of which is connected via a gateway or modem to the internet while the other is connected to the secure internal network. In such a situation, the first adapter would be configured as untrusted, since it is exposed to traffic from the outside world. Assuming the internal network is protected by the firewall and other intrusion prevention measures, the second adapter can be considered to be trustworthy.
The customization screen of the lokkit tool displays a list of detected network interfaces. To designate a device as trusted, tab to the device entry next to Trusted Devices and select it with the space key. An asterisk will appear indicating that the device is now trusted.
Masquerading
Masquerading is better known in networking circles as Network Address Translation (NAT). When using an RHEL system as a gateway to the internet for a network of computers, masquerading allows all of the internal systems to use the IP address of the RHEL system when communicating over the internet. This has the advantage of hiding the internal IP addresses of any systems from malicious external entities and also avoids the necessity to allocate a public IP address to every computer on the network. This service is also provided by most routers and gateways so this feature of the RHEL Firewall is rarely used.