Creating an Ubuntu 10.x KVM Networked Bridge Interface
| Previous | Table of Contents | Next |
| Installing and Configuring Ubuntu 10.x KVM Virtualization | Installing an Ubuntu 10.x KVM Guest OS from the Command-line (virt-install and virsh) |
By default, the KVM virtualization environment on Ubuntu only creates a virtual network to which virtual machines may connect. The goal of this chapter is to cover the steps involved in creating a network bridge on Ubuntu enabling guest systems to share one or more of the host system’s physical network connections.
Ubuntu Virtual Networks and Network Bridges
A KVM virtual machine running on Ubuntu has two options in terms of networking connectivity. One option is for it to be connected to a virtual network running within the operating system of the host computer. In this configuration any virtual machines on the virtual network can see each other but access to the external network is provided by Network Address Translation (NAT). When using the virtual network and NAT, each virtual machine is represented on the external network (the network to which the host is connected) using the IP address of the host system. This is the default behavior for KVM virtualization and requires no additional configuration, other than selecting the Virtual network option on the advanced settings section of the summary screen of the virt-manager new virtual machine wizard. Typically, a single virtual network is created by default, represented by the name default and the device virbr0.
In order for guests to appear as individual and independent systems on the external network (i.e. with their own IP addresses), they must be configured to share a physical network interface on the host. This is achieved by configuring a network bridge interface on the host system to which the guests can connect. In the remainder of this chapter we will cover the steps necessary to configure an Ubuntu network bridge for use by KVM based guest operating systems.
Installing the Network Bridge Package Requirements
The creation of a network bridge involves the use of the qemu, libcap2-bin and bridge-utils packages, each of which may be installed from within a terminal window using the following command:
sudo apt-get install qemu libcap2-bin bridge-utils
Configuring Network Administration Capabilities
In order to allow the creation of a network bridge it is first necessary to allocate some network configuration permissions to the current user (i.e. the user that will be logged in during the bridge creation process). The first step in achieving this goal is to run the following command in a terminal window:
For 64-bit Ubuntu hosts:
sudo setcap cap_net_admin=ei /usr/bin/qemu-system-x86_64
For 32-bit Ubuntu hosts:
sudo setcap cap_net_admin=ei /usr/bin/qemu-system-i386
Next, edit the /etc/security/capability.conf file using your preferred editor. For example:
sudo gedit /etc/security/capability.conf
Within the editor, add a line to the file that reads as follows (where <username> is replaced by the user that will be logged in when the network bridge is created):
cap_net_admin <username>
Once the line has been added, save the file and exit from the editor.
Identifying Physical Network Connections
With the requisite packages installed and permissions configured it is now time to look at the current network configuration. The easiest way to do this is to run the ifconfig command. The following shows output from running ifconfig on a system on which KVM is installed, but on which a network bridge has yet to be configured:
eth0 Link encap:Ethernet HWaddr 00:18:e7:16:da:65
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Interrupt:16 Base address:0xb800
eth1 Link encap:Ethernet HWaddr 00:13:72:0b:14:57
inet addr:192.168.2.18 Bcast:192.168.2.255 Mask:255.255.255.0
inet6 addr: fe80::213:72ff:fe0b:1457/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:13561 errors:0 dropped:0 overruns:0 frame:0
TX packets:5833 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:7549871 (7.5 MB) TX bytes:784862 (784.8 KB)
Interrupt:17 Memory:fe3e0000-fe400000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:96383 errors:0 dropped:0 overruns:0 frame:0
TX packets:96383 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:175806587 (175.8 MB) TX bytes:175806587 (175.8 MB)
virbr0 Link encap:Ethernet HWaddr 00:00:00:00:00:00
inet addr:192.168.122.1 Bcast:192.168.122.255 Mask:255.255.255.0
inet6 addr: fe80::7ce4:c9ff:fe4f:d4c0/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:5308 errors:0 dropped:0 overruns:0 frame:0
TX packets:6351 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:417587 (417.5 KB) TX bytes:6691251 (6.6 MB)
In the above output, the entry for eth1 represents a physical network adaptor on the host computer with a presence on the external network represented by the IP address 192.168.2.18. This is the connection currently used by this host to access the external network. The virbr0 entry represents the virtual network to which guest operating systems will connect if configured to do so.
In order to provide the option for guest operating systems to share the eth1 connection of the host it is necessary to establish a network bridge between eth1 and the virtual machines.
Configuring the Network Bridge
Begin the bridge creation process by editing the /etc/network/interfaces file:
sudo gedit /etc/network/interfaces
If you would like the network bridge to obtain an IP address from a DHCP server on the external network, modify the file so that it reads as follows (keeping in mind that your network device may not be eth1):
auto lo
iface lo inet loopback
auto eth1
iface eth1 inet manual
auto br0
iface br0 inet dhcp
bridge_ports eth1
bridge_stp off
bridge_fd 0
bridge_maxwait 0
If, on the other hand, you would like to assign static IP information to the bridge device, modify the file accordingly (substituting your own static IP information in place of the example values provided):
auto lo
iface lo inet loopback
auto eth1
iface eth1 inet manual
auto br0
iface br0 inet static
address 192.168.2.100
network 192.168.2.0
netmask 255.255.255.0
broadcast 192.168.2.255
gateway 192.168.2.1
bridge_ports eth1
bridge_stp off
bridge_fd 0
bridge_maxwait 0
Once the changes have been made, save the configuration file and exit from the editor session. Finally, restart the networking services on the host using the following command:
sudo /etc/init.d/networking restart
Checking for the Presence of the Bridge
Using the ifconfig command once again, the new bridge interface should now be visible:
br0 Link encap:Ethernet HWaddr 00:13:72:0b:14:57
inet addr:192.168.2.18 Bcast:255.255.255.255 Mask:255.255.255.0
inet6 addr: fe80::213:72ff:fe0b:1457/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:3823 errors:0 dropped:0 overruns:0 frame:0
TX packets:2193 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:4433459 (4.4 MB) TX bytes:199714 (199.7 KB)
eth0 Link encap:Ethernet HWaddr 00:18:e7:16:da:65
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Interrupt:16 Base address:0xb800
eth1 Link encap:Ethernet HWaddr 00:13:72:0b:14:57
inet6 addr: fe80::213:72ff:fe0b:1457/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:17417 errors:0 dropped:0 overruns:0 frame:0
TX packets:8184 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:12075177 (12.0 MB) TX bytes:1003193 (1.0 MB)
Interrupt:17 Memory:fe3e0000-fe400000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:105767 errors:0 dropped:0 overruns:0 frame:0
TX packets:105767 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:204343793 (204.3 MB) TX bytes:204343793 (204.3 MB)
virbr0 Link encap:Ethernet HWaddr 00:00:00:00:00:00
inet addr:192.168.122.1 Bcast:192.168.122.255 Mask:255.255.255.0
inet6 addr: fe80::7ce4:c9ff:fe4f:d4c0/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:5308 errors:0 dropped:0 overruns:0 frame:0
TX packets:6373 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:417587 (417.5 KB) TX bytes:6692359 (6.6 MB)
vnet0 Link encap:Ethernet HWaddr fe:54:00:85:24:05
inet6 addr: fe80::fc54:ff:fe85:2405/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:152 errors:0 dropped:0 overruns:0 frame:0
TX packets:524 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:17403 (17.4 KB) TX bytes:77444 (77.4 KB)
Configuring the Ubuntu Firewall for a Network Bridge
If a firewall is enabled on the Ubuntu host, it may be necessary to add an iptables rule to allow network traffic via the bridge interface. This is achieved by adding a rule similar to the following to the /etc/sysconfig/iptables configuration file:
-A RH-Firewall-1-INPUT -i br0 -j ACCEPT
Configuring a Virtual Machine to use the Network Bridge
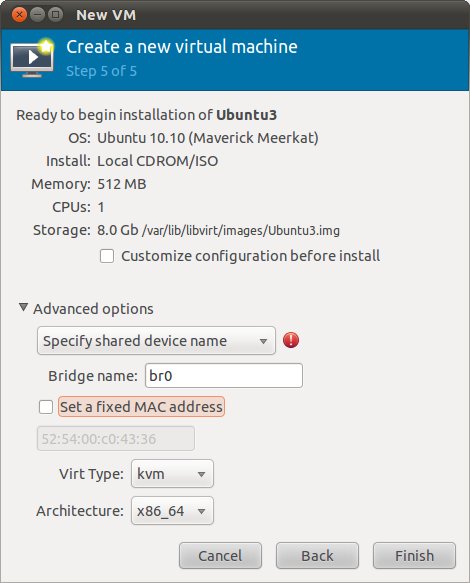
Within the virt-manager tool, the networking menu under the Advanced options section of the final page of the new virtual machine creation wizard includes an option to Specify shared device name. Select this option and enter the name of the bridge (in this case br0) into the text box provided:
When this option is selected for a virtual machine it will have access to the external network using the same physical network device used by the host, but now using its own IP address.
| Previous | Table of Contents | Next |
| Installing and Configuring Ubuntu 10.x KVM Virtualization | Installing an Ubuntu 10.x KVM Guest OS from the Command-line (virt-install and virsh) |